 GETTY IMAGES
GETTY IMAGES
A leading medical-research institution working on a cure for Covid-19 has admitted it paid hackers a $1.14m (£910,000) ransom after a covert negotiation witnessed by BBC News.
The Netwalker criminal gang attacked University of California San Francisco (UCSF) on 1 June.
IT staff unplugged computers in a race to stop the malware spreading.
And an anonymous tip-off enabled BBC News to follow the ransom negotiations in a live chat on the dark web.
Cyber-security experts say these sorts of negotiations are now happening all over the world - sometimes for even larger sums - against the advice of law-enforcement agencies, including the FBI, Europol and the UK's National Cyber Security Centre.
Netwalker alone has been linked to at least two other ransomware attacks on universities in the past two months.
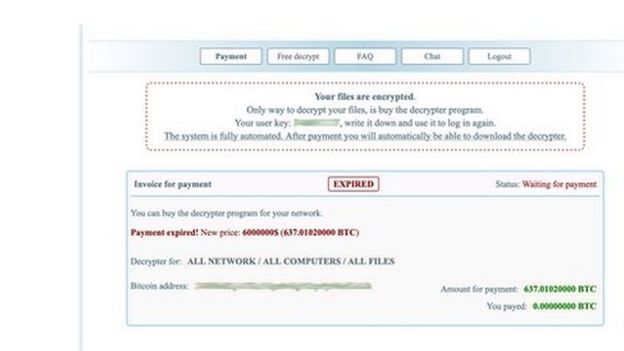
At first glance, its dark-web homepage looks like a standard customer-service website, with a frequently asked questions (FAQ) tab, an offer of a "free" sample of its software and a live-chat option.
But there is also a countdown timer ticking down to a time when the hackers either double the price of their ransom, or delete the data they have scrambled with malware.
Instructed to log in - either by email or a ransom note left on hacked computer screens - UCSF was met with the following message, posted on 5 June.
![Hacker chat box saying [Operator]: 'Hi UCSF, don't be shy we can work together on the current incident'](https://ichef.bbci.co.uk/news/624/cpsprodpb/2B92/production/_113145111_chatbox1new2.jpg)
Six hours later, the university asked for more time and for details of the hack to be removed from Netwalker's public blog.
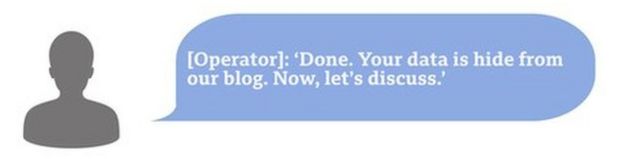
Noting UCSF made billions a year, the hackers then demanded $3m
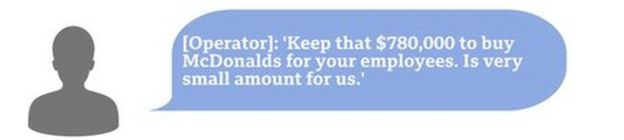
But the UCSF representative, who may be an external specialist negotiator, explained the coronavirus pandemic had been "financially devastating" for the university and begged them to accept $780,000.

After a day of back-and-forth negotiations, UCSF said it had pulled together all available money and could pay $1.02m - but the criminals refused to go below $1.5m.

Hours later, the university came back with details of how it had procured more money and a final offer of $1,140,895.

And the next day, 116.4 bitcoins were transferred to Netwalker's electronic wallets and the decryption software sent to UCSF.
UCSF is now assisting the FBI with its investigations, while working to restore all affected systems.
It told BBC News: "The data that was encrypted is important to some of the academic work we pursue as a university serving the public good.
"We therefore made the difficult decision to pay some portion of the ransom, approximately $1.14 million, to the individuals behind the malware attack in exchange for a tool to unlock the encrypted data and the return of the data they obtained.
"It would be a mistake to assume that all of the statements and claims made in the negotiations are factually accurate."
 IBRAVE
IBRAVE
But Jan Op Gen Oorth, from Europol, which runs a project called No More Ransom, said: "Victims should not pay the ransom, as this finances criminals and encourages them to continue their illegal activities.
"Instead, they should report it to the police so law enforcement can disrupt the criminal enterprise."
Brett Callow, a threat analyst at cyber-security company Emsisoft, said: "Organisations in this situation are without a good option.
"Even if they pay the demand, they'll simply receive a pinky-promise that the stolen data will be deleted.
"But why would a ruthless criminal enterprise delete data that it may be able to further monetise at a later date?"
Most ransomware attacks begin with a booby-trapped emaiI and research suggests criminal gangs are increasingly using tools that can gain access to systems via a single download. In the first week of this month alone, Proofpoint's cyber-security analysts say they saw more than one million emails with using a variety of phishing lures, including fake Covid-19 test results, sent to organisations in the US, France, Germany, Greece, and Italy.
Organisations are encouraged to regularly back-up their data offline.
But Proofpoint's Ryan Kalember said: "Universities can be challenging environments to secure for IT administrators.
"The constantly changing student population, combined with a culture of openness and information-sharing, can conflict with the rules and controls often needed to effectively protect the users and systems from attack."





